vRA 8.x and Azure AD MFA
I was looking into, if you could enable Azure AD Multi Factor Authentication on VMware vRealize Automation, have not found anything abount if this is supported or not.
Before enabling this make sure you have snapshots of the VMware Identity Manager (vIDM), and that you have granted the you have add you AD admin account to the vIDM “Super Admin” role, so you can revert the configuration, if you need to.
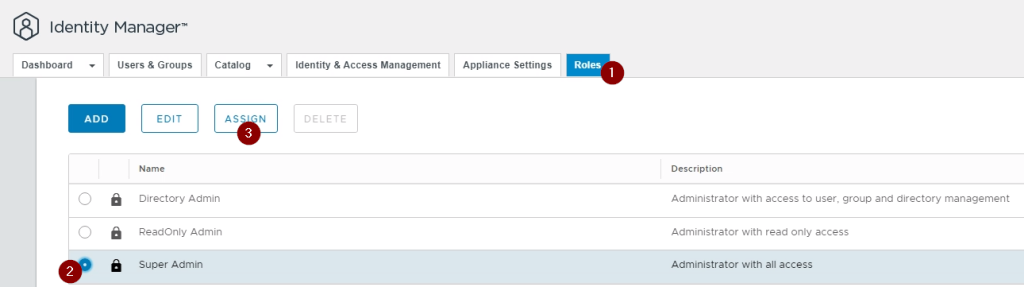
You still need to setup the AD connection in the vIDM, like normal.
the you have to setup a Azure AD Sync, I am not an expert on Azure AD, so I will not wriyr about how to do that, only how to the setup is, when using it together with vRA 8.x, the Azure AD Sync must be running and synchronizing the same users and groups, that you are synchronizing in the vIDM.
Azure AD tasks
In the Azure portal you have to go into “Azure Active Directory”.

Here you need to create a “Enterprise Application”.

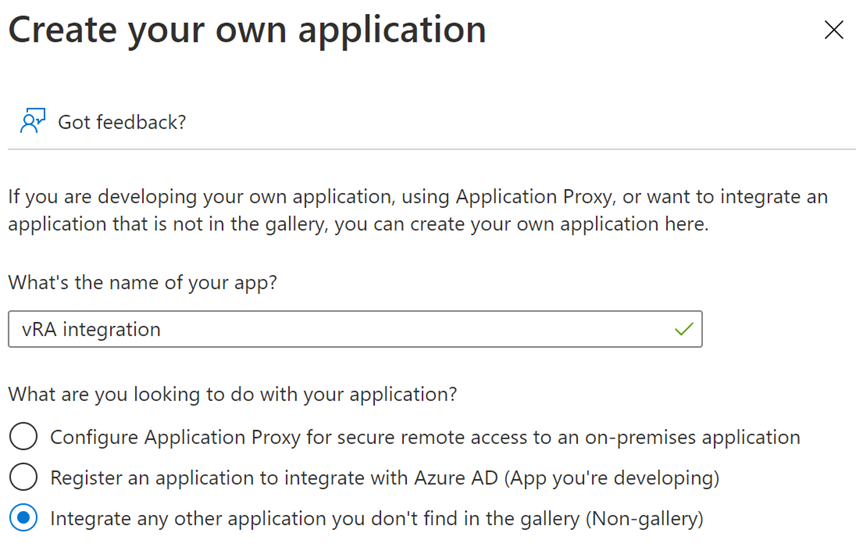
Give the application a good name, and choose “Integrate any other application……”.
Assign users and groups.

Add the same users and groups that is assigned in the vRA.
Now we need to setup the SSO settings.
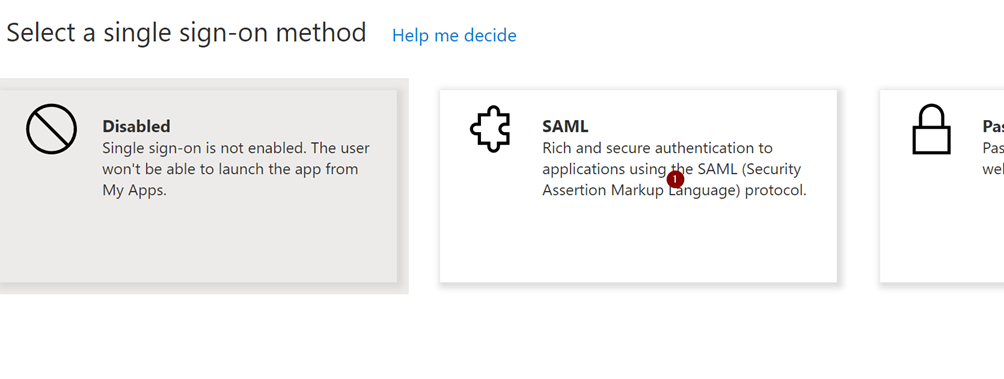
Select the SAML configuration.
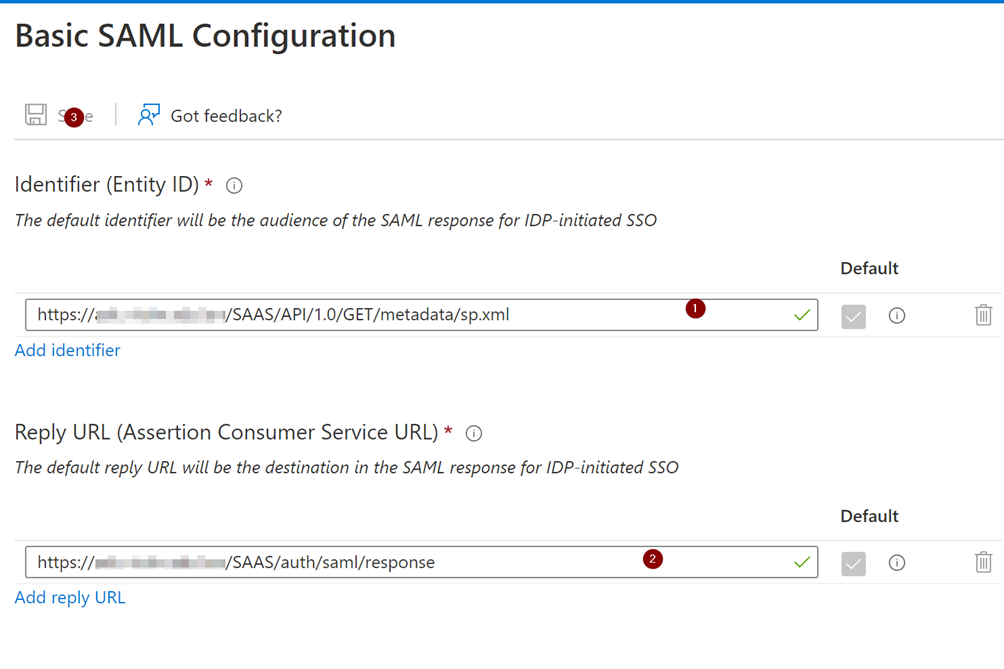
https://<vIDM FQDN>/SAAS/API/1.0/GET/metadata/sp.xml
https://<vIDM FQDN>/SAAS/auth/saml/response
Now we need to configure the “Attributes & Claims”.
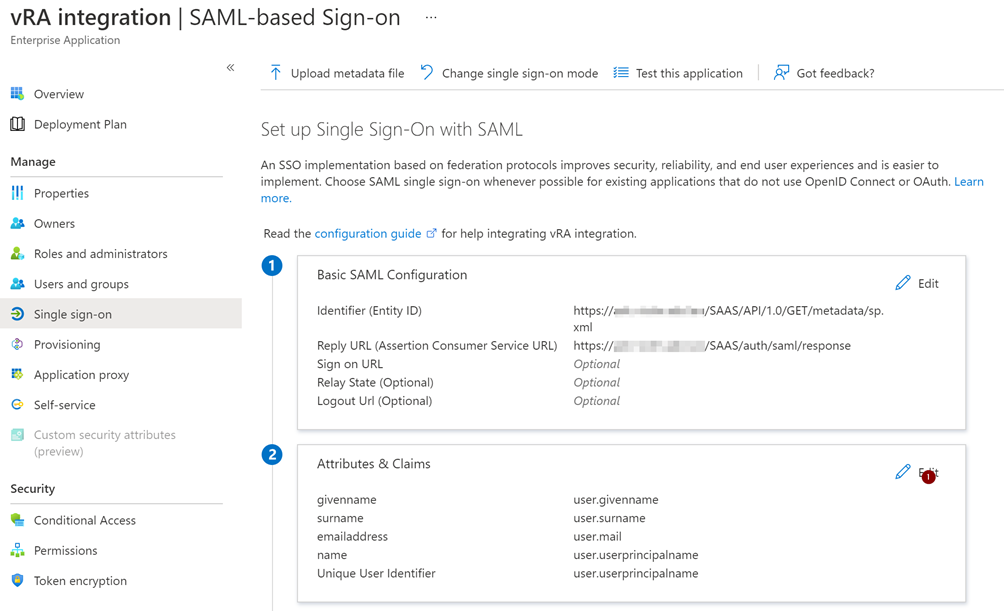
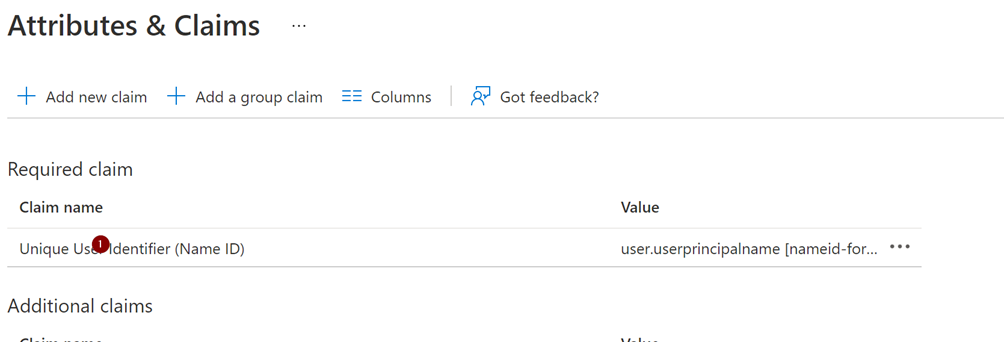
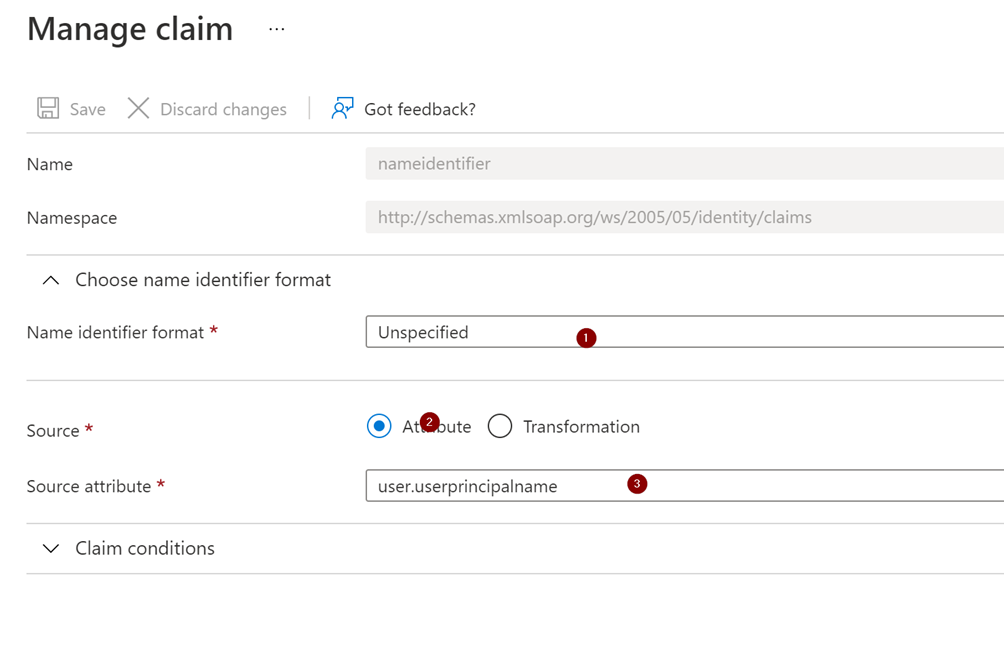
Set the “Name identifier format” to “Unspecified” and the source Attribite to “user:userprinciplaname”.
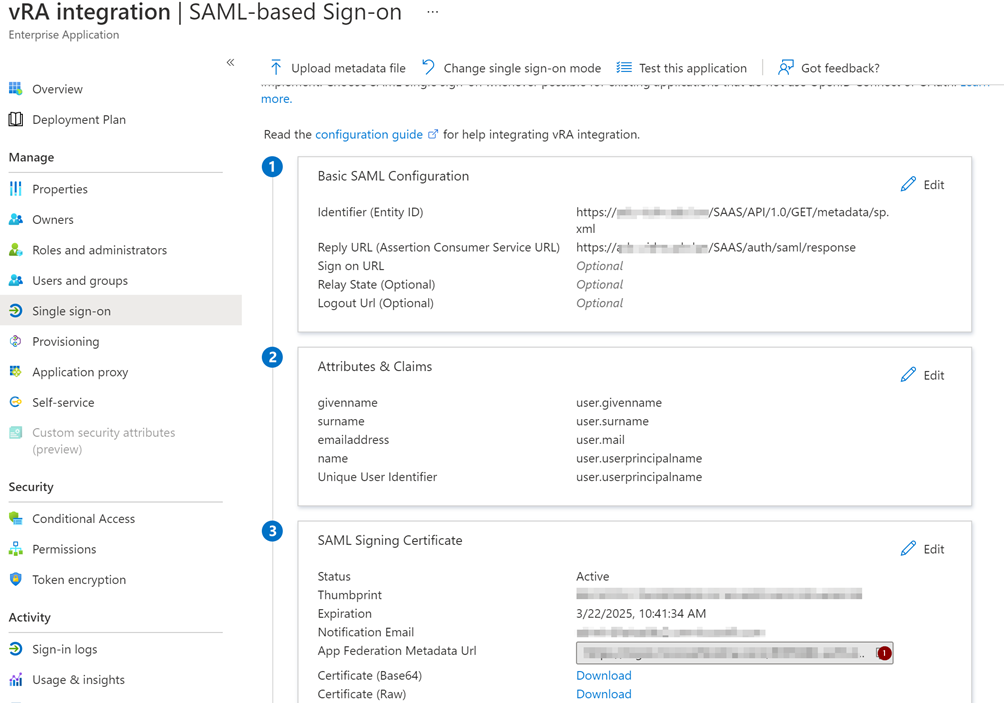
Now copy the “App Federation Metadata Url” we will need this later.
vIDM configuration
In the vIDM we need to set up a “Identity Provider”.
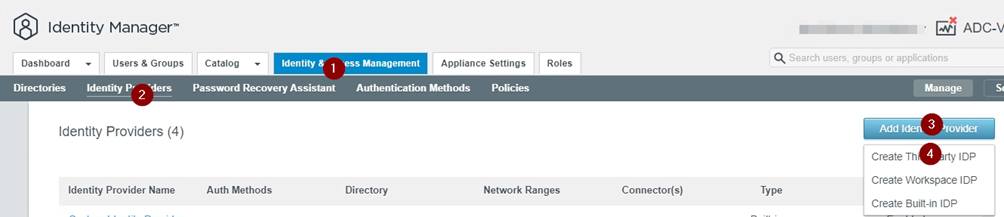
Create “Third party IDP”.
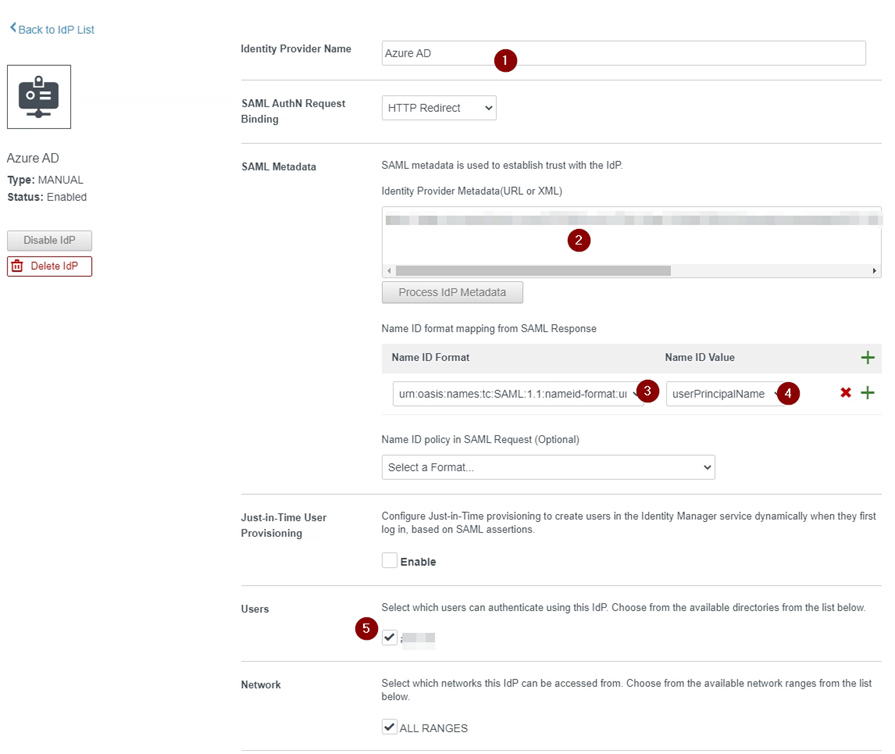
Give a good name:
In the SAML Metadata, “Identity Provider Metadata(URL or XML)” insert the link copied from the last step in the Azure AD configuration.
Select the AD Domain that the users, are login into, and that are configured in the vIDM.
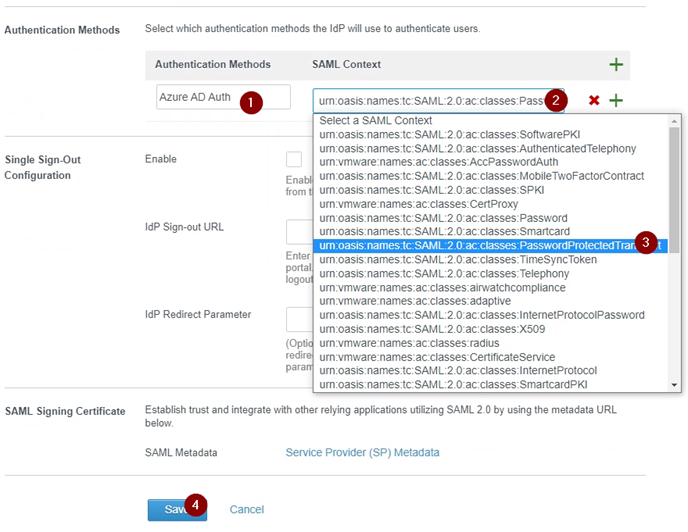
Create a “Authentication Methods”, give it a good name, and select the “urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport”.
and save the configuration
Now we need to enable this on the login page.
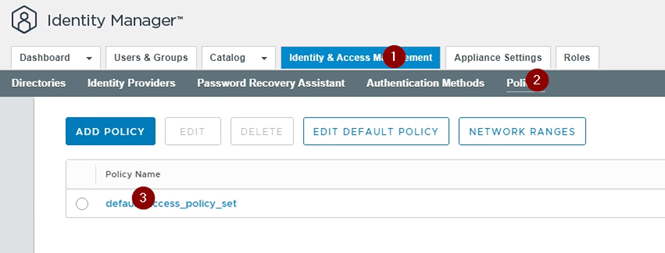
configure the default profile access policy.
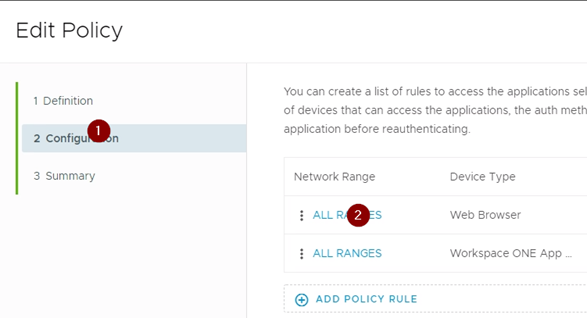
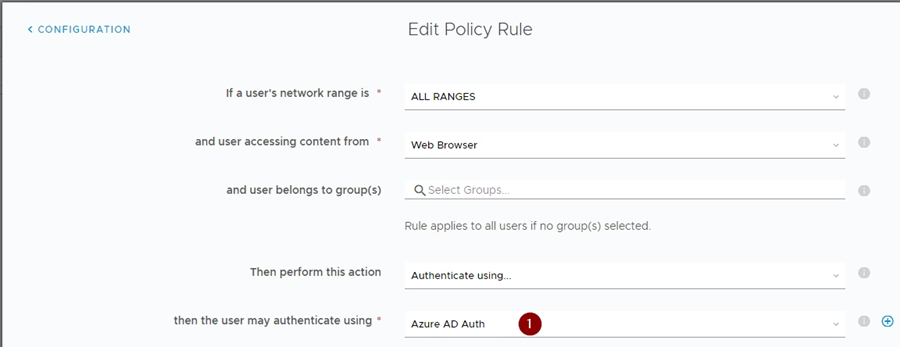
In the “then the user may authenticate using” to the new third party IDP, “Authentication Method” you just created.
Notes
Not sure if this i supported by VMware, so use at you own risk.
This may not be the best way of doing this, but it work for me in the lab.
When enable like above, you can not login with users from the local domain, except thru the API.
The vRA API do not use the policy, so this will not require MFA.
I have only tested this with vRA version 8.6.2 and vIDM 3.3.6.
You don’t have to sync AD first, if you just JustInTime provisioning.